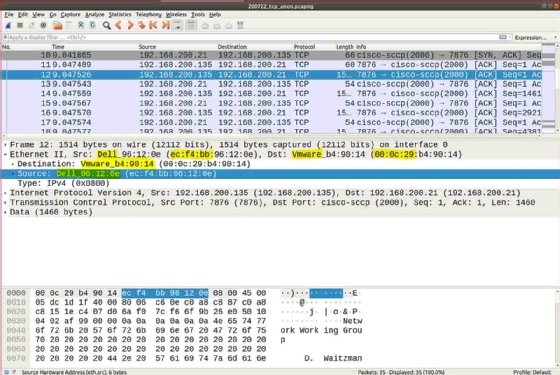
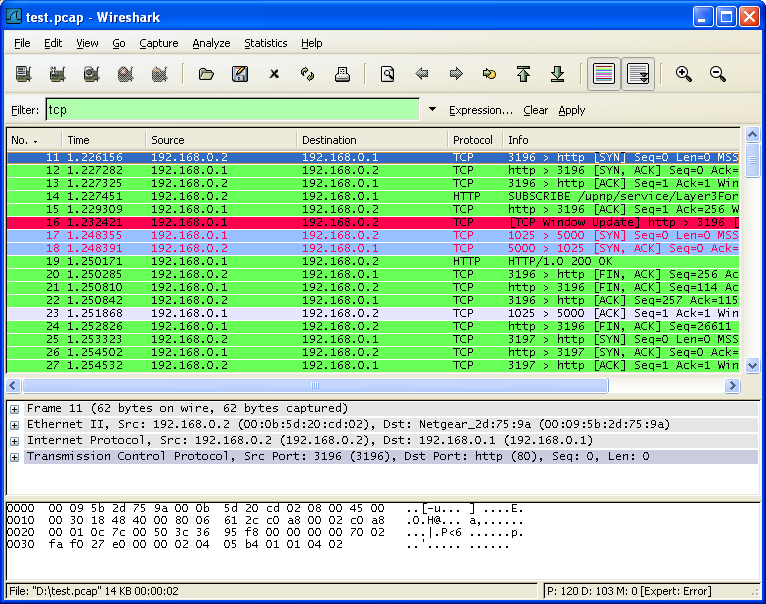
Wireshark is a widely used, open-source network protocol analyzer that allows users to capture and inspect network traffic in real time. It is an essential tool for network administrators, cybersecurity professionals, and developers for troubleshooting network issues, analyzing network performance, and detecting security vulnerabilities. Wireshark provides detailed insights into network packets, protocols, and communication patterns.
Features:
- Packet Capture: Captures and analyzes network traffic from various interfaces, including Ethernet, Wi-Fi, and more.
- Detailed Analysis: Provides in-depth analysis of network packets, including headers, payloads, and protocol details.
- Filtering and Searching: Allows users to filter and search through captured traffic based on various criteria, such as protocol type, IP address, and port number.
- Protocol Decoding: Supports a wide range of network protocols and can decode and display protocol-specific information.
- Graphical Interface: Features an intuitive graphical user interface (GUI) for easy navigation, packet inspection, and analysis.
Technical Application Details:
- Software Full Name: Wireshark
- Setup File Name: Wireshark-winxx-x.y.z.exe (for Windows) / wireshark-x.y.z.tar.xz (for Linux) / Wireshark-x.y.z.dmg (for macOS) (assumed, as file names may vary)
- Full Setup Size: Approximately 50-100 MB
- Setup Type: Installer
- Compatibility Architecture: 32-bit (x86) / 64-bit (x64)
System Requirements for Wireshark:
- Operating System: Windows 7, 8, 10, 11 / Linux / macOS
- Memory (RAM): Minimum 2 GB of RAM required
- Hard Disk Space: 200 MB of free space required for installation
- Processor: Any modern CPU
- Developers: Wireshark Foundation
Important Note: Wireshark is a powerful tool for network analysis and troubleshooting, and it is widely used in legitimate network management and security assessments. However, capturing and analyzing network traffic without proper authorization can lead to legal and ethical issues, including privacy violations. Always ensure that you have appropriate permissions and follow legal and ethical guidelines when using Wireshark or similar network analysis tools. It is crucial to use such tools responsibly to maintain the integrity and confidentiality of network communications.





0 comments: