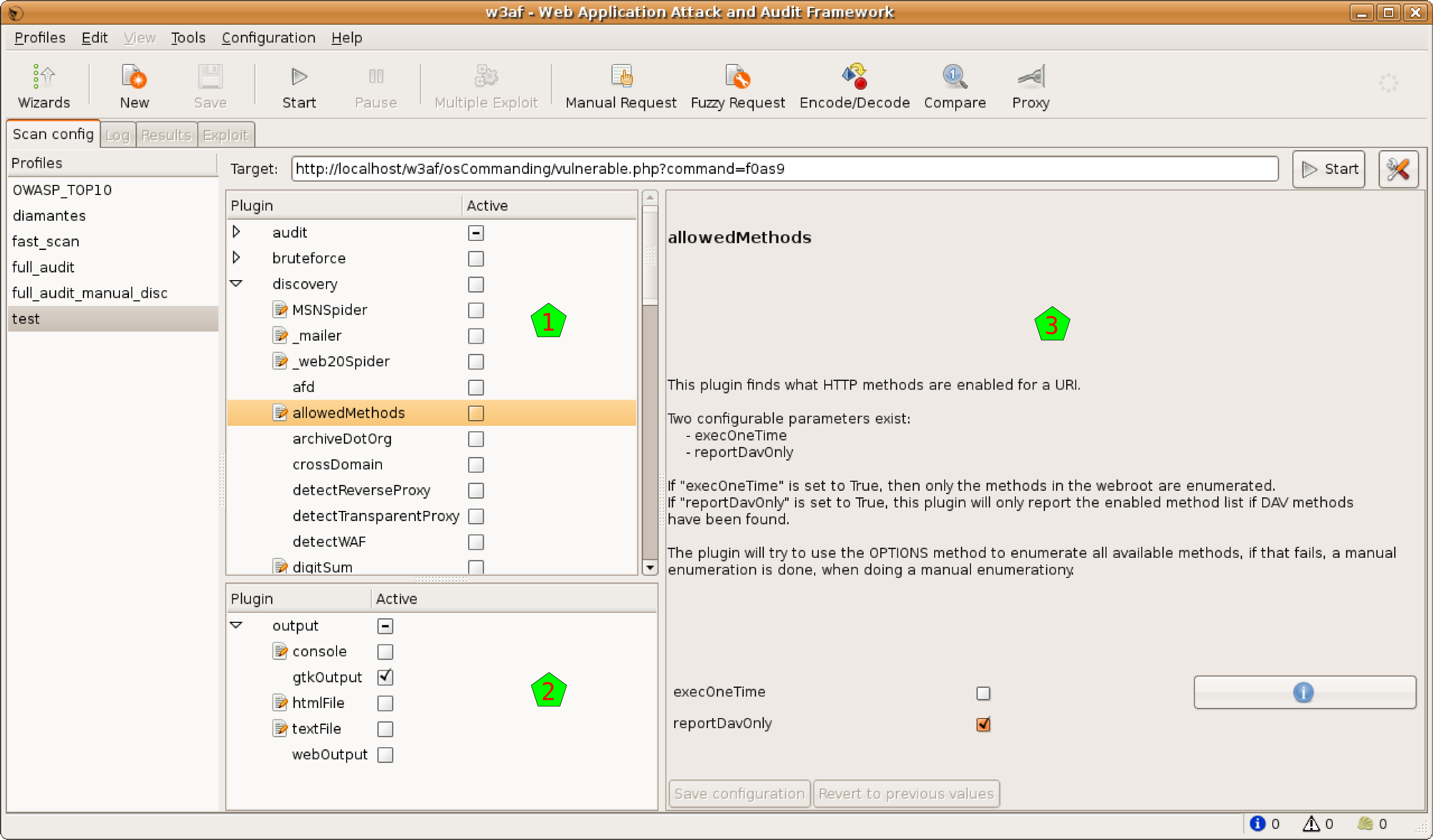
w3af (Web Application Attack and Audit Framework) is an open-source web application security scanner and assessment tool. It is designed to help security professionals identify and analyze vulnerabilities in web applications. w3af provides a range of features for discovering security flaws, including SQL injection, cross-site scripting (XSS), and other common vulnerabilities. Its modular architecture allows users to extend and customize its functionality.
Features:
- Automated Scanning: Performs automated scans to identify various web application vulnerabilities, such as SQL injection, XSS, and file inclusion.
- Plugin Architecture: Modular design with a wide range of plugins for different types of vulnerability testing and web application analysis.
- Comprehensive Reporting: Generates detailed reports on detected vulnerabilities, including descriptions, impact assessments, and recommendations for remediation.
- Customizable Scanning: Allows for customization of scan settings, including specific attack vectors and scanning techniques.
- Command-Line and GUI Interface: Provides both command-line and graphical user interface (GUI) options for ease of use and flexibility.
Technical Application Details:
- Software Full Name: w3af (Web Application Attack and Audit Framework)
- Setup File Name: w3af-x.y.z.tar.gz (for Linux) / w3af-x.y.z.exe (for Windows) (assumed, as file names may vary)
- Full Setup Size: Approximately 50-150 MB
- Setup Type: Compressed Archive (Tar/Gzip) / Installer
- Compatibility Architecture: 32-bit (x86) / 64-bit (x64)
System Requirements for w3af:
- Operating System: Windows 7, 8, 10, 11 / Linux / macOS
- Memory (RAM): Minimum 1 GB of RAM required
- Hard Disk Space: 100 MB of free space required for installation
- Processor: Any modern CPU
- Developers: Andres Riancho
Important Note: w3af is a powerful tool for web application security assessment and vulnerability testing. It is intended for use by security professionals, developers, and researchers to identify and mitigate security issues in web applications. Always ensure that any testing conducted with w3af is authorized and performed with proper consent. Unauthorized scanning or testing of web applications without permission is illegal and unethical. Adhere to legal and ethical guidelines in cybersecurity practices and use w3af responsibly to protect and secure web applications.











0 comments: