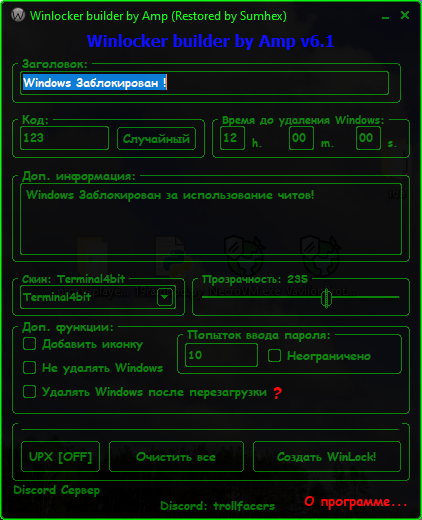
Winlocker Builder is a tool designed to create ransomware known as "winlockers." Winlockers are a type of malware that locks or restricts access to a user's system or files until a ransom is paid. The tool allows users to customize and build their own Winlocker variants, which can then be used to lock systems and demand payment from victims.
Ad Space 300x250
Buy NowPopular Posts
-
Burp Suite is a comprehensive web vulnerability scanner and security testing platform designed for penetration testers and security profess...
-
Bat To Exe Converter is a utility software that converts batch script files (.bat) into executable files (.exe). This tool is commonly used ...
-
OllyDbg is a popular and advanced 32-bit assembler-level debugger for Windows. It is widely used by reverse engineers and security research...
-
NFCGate is an Android application designed for testing and exploiting Near Field Communication (NFC) technology. It allows users to capture,...
-
SpyMAX is an Android Remote Administration Tool (RAT) that allows remote control and monitoring of Android devices. It provides users with ...
-
WebCruiser Web Vulnerability Scanner is a security tool designed to identify and assess vulnerabilities in web applications. It automates t...
-
PowerArchiver is a versatile file compression and archiving tool for Windows. It allows users to create, extract, and manage compressed file...
Blog Archive
Labels Cloud
Ad Space 300x250
Buy Now










0 comments: