P4wnP1 A.L.O.A. is a penetration testing and security assessment tool designed for use with the p4wnp1 hardware platform. It provides a range of functionalities for security testing, including wireless network attacks, credential harvesting, and network sniffing. The tool is commonly used by cybersecurity professionals and ethical hackers to assess the security of systems and networks.
Features:
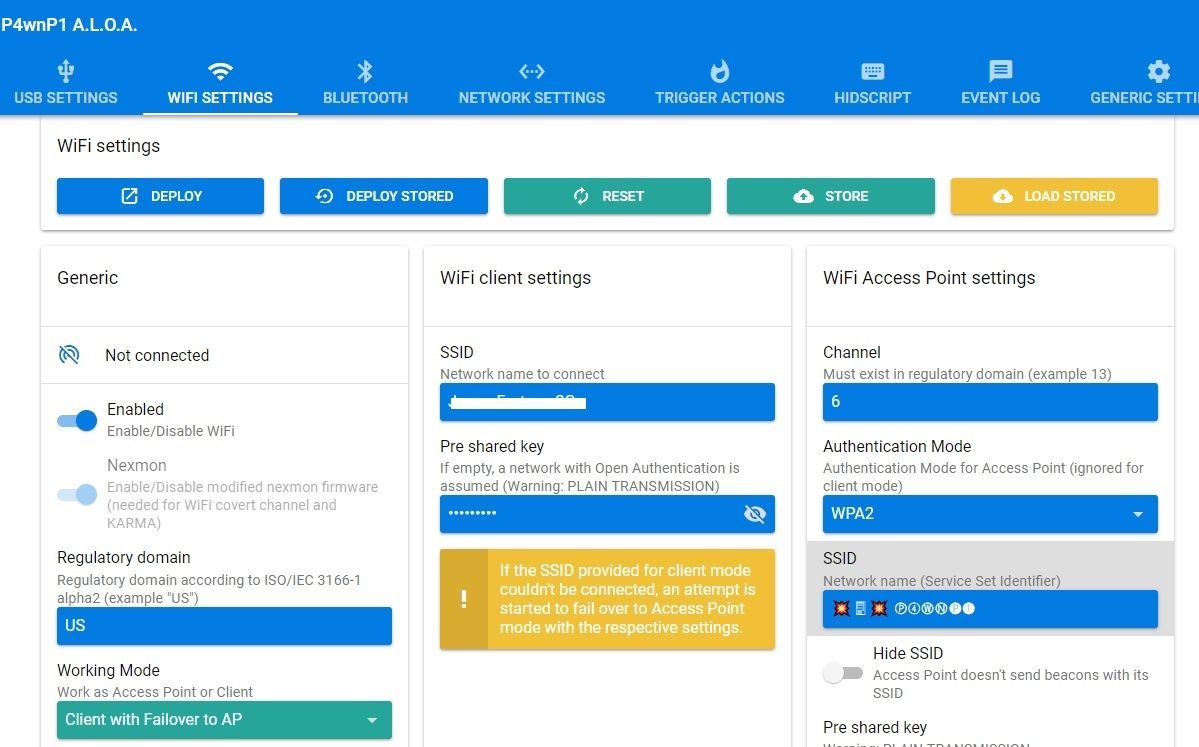
- Wireless Network Attacks: Perform attacks on wireless networks, including de-authentication and packet injection.
- Credential Harvesting: Collect and analyze credentials from network traffic and authentication attempts.
- Network Sniffing: Monitor and capture network traffic for analysis and security assessment.
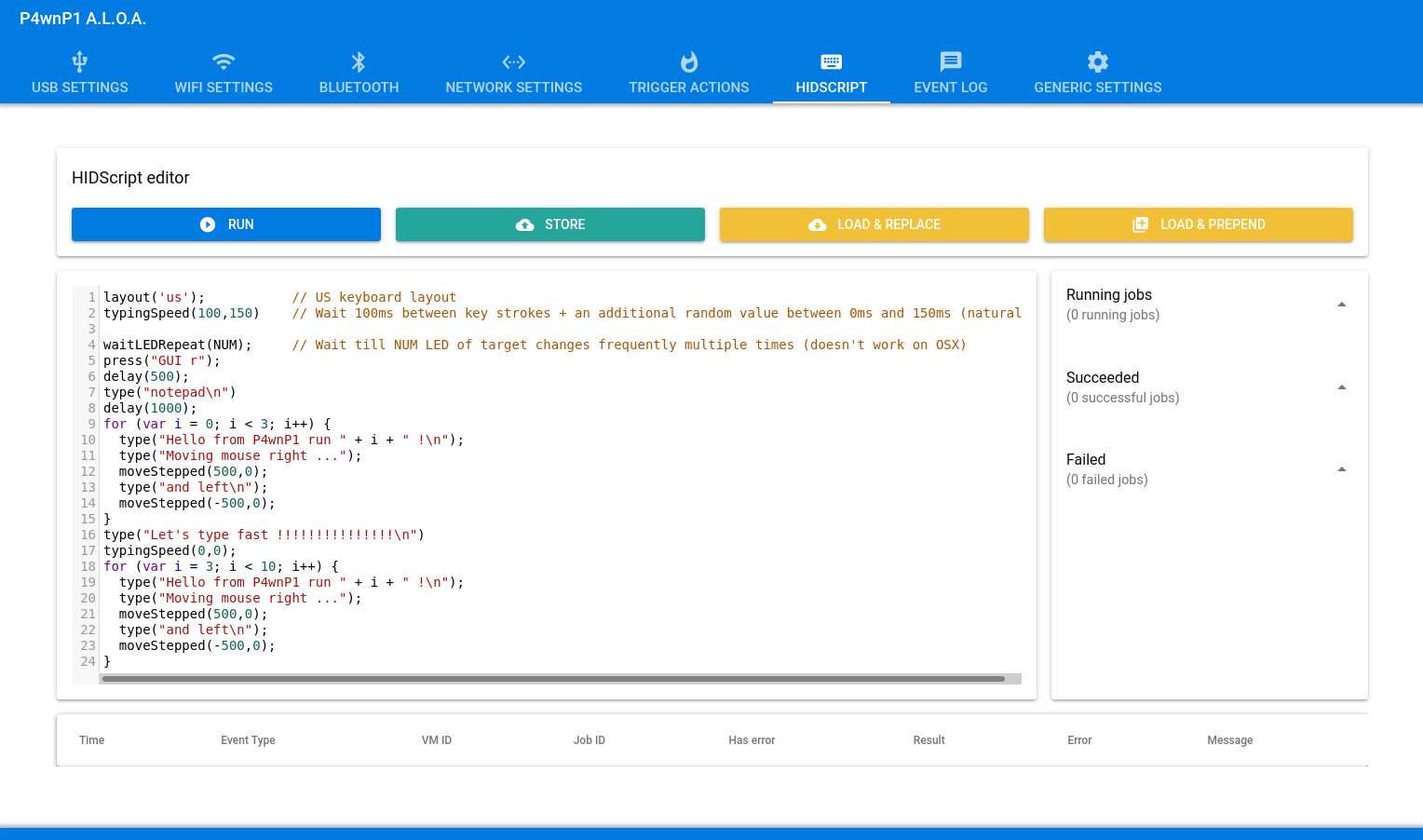
- Scriptable Interface: Offers a scripting interface for automating tasks and creating custom security tests.
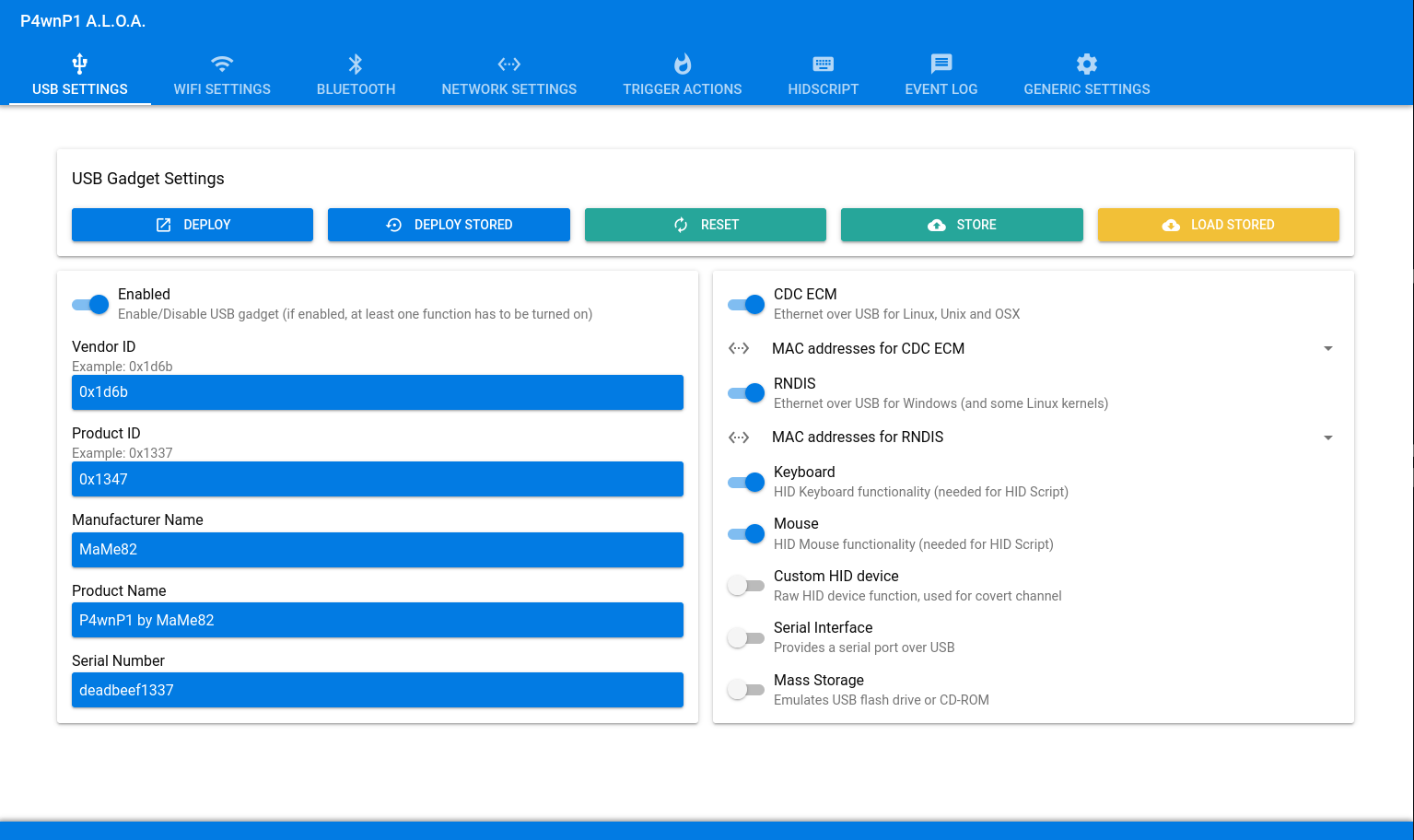
- Integration with p4wnp1: Designed to work with the p4wnp1 hardware platform for extended functionality.
Technical Application Details:
- Software Full Name: P4wnP1 A.L.O.A.
- Setup File Name: p4wnp1-aloa.tar.gz (or similar, depending on distribution)
- Full Setup Size: Approximately 20-30 MB
- Setup Type: Compressed Archive (requires extraction and setup)
- Compatibility Architecture: ARM / x86 (varies by p4wnp1 hardware and software environment)
System Requirements for P4wnP1 A.L.O.A.:
- Operating System: Compatible with Linux-based systems used with p4wnp1 hardware
- Memory (RAM): Minimum 512 MB of RAM required
- Hard Disk Space: 50 MB of free space required for installation
- Processor: Any modern ARM or x86 processor compatible with p4wnp1 hardware
- Developers: MaMe82
Important Note: P4wnP1 A.L.O.A. is intended for use in penetration testing and security assessment. It should be used ethically and legally, with explicit permission to test and analyze systems and networks. Unauthorized use of security testing tools can lead to legal consequences and damage to network security. Always follow ethical guidelines and obtain proper authorization before conducting any security assessments or tests.










0 comments: