DIVA-Android (Damn Insecure and Vulnerable App) is a purposely vulnerable Android application designed for security training and testing. It is used by cybersecurity professionals and researchers to practice and learn about common security vulnerabilities in Android applications. The app is intentionally designed with multiple security flaws to help users understand how to identify, exploit, and mitigate these vulnerabilities.
Features:
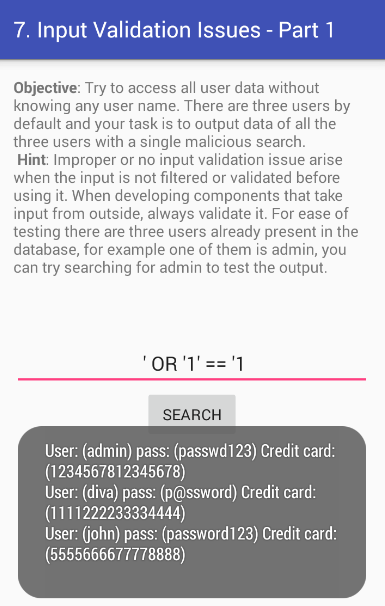
- Vulnerability Simulation: Contains multiple known vulnerabilities, including insecure data storage, insufficient encryption, and improper validation.
- Educational Tool: Serves as a practical learning resource for understanding Android security issues and best practices.
- Hands-On Testing: Allows users to practice security testing techniques and tools in a controlled environment.
- Realistic Scenarios: Mimics real-world security flaws to provide a realistic training experience.
Technical Application Details:
- Software Full Name: DIVA-Android (Damn Insecure and Vulnerable App)
- Setup File Name: diva-android.apk
- Full Setup Size: Approximately 10-20 MB
- Setup Type: APK File (for Android installation)
- Compatibility Architecture: ARM / x86 (varies by Android device architecture)
System Requirements for DIVA-Android:
- Operating System: Android 4.4 and above
- Memory (RAM): Minimum 512 MB of RAM required
- Hard Disk Space: 20 MB of free space required for installation
- Processor: Any modern ARM or x86 processor
- Developers: payatu
Important Note: DIVA-Android is a valuable tool for learning and practicing Android application security. It is intended for educational purposes only and should not be used for malicious activities. Users should ensure that they only perform security testing on applications and systems for which they have explicit permission. Ethical guidelines and legal standards must be followed to avoid unauthorized access and potential legal consequences.











0 comments: