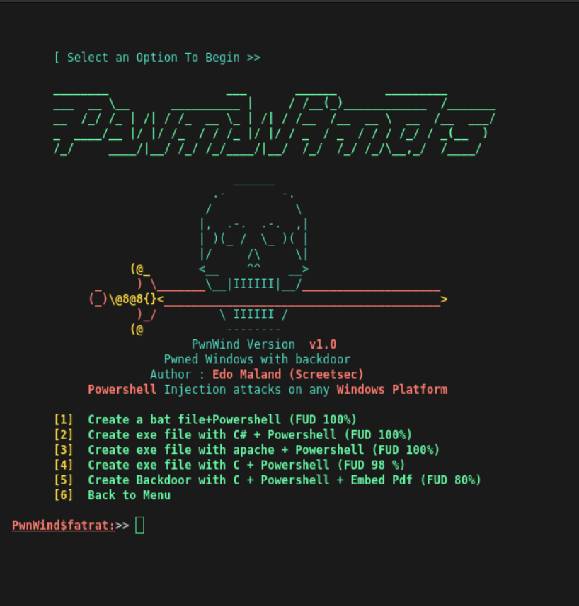
TheFatRat is a powerful and versatile open-source tool used for generating malicious payloads and backdoors for penetration testing and security research. It is designed to simplify the creation of executable files that can be used for ethical hacking and security assessments. TheFatRat supports various payload types and offers features for payload customization and delivery.
Ad Space 300x250
Buy NowPopular Posts
-
P2Pover is a network management tool primarily used for controlling and monitoring peer-to-peer (P2P) traffic on a network. It is designed ...
-
CyberGate RAT (Remote Access Trojan) v1.01.12 is a type of malware that provides attackers with remote control over infected systems. Develo...
-
njRAT v0.7d , developed by a hacker known as njq8, is a remote access tool (RAT) widely used by cybercriminals to gain unauthorized access ...
-
888-RAT (Remote Access Trojan) is a type of malware designed to provide remote access and control over an infected computer. It allows atta...
-
NFCGate is an Android application designed for testing and exploiting Near Field Communication (NFC) technology. It allows users to capture,...
-
Disable Windows Defender v1.1 is a tool designed to permanently disable Microsoft Windows Defender, the built-in antivirus and anti-malware...
-
SpyMAX is an Android Remote Administration Tool (RAT) that allows remote control and monitoring of Android devices. It provides users with ...
Blog Archive
Labels Cloud
Ad Space 300x250
Buy Now










0 comments: