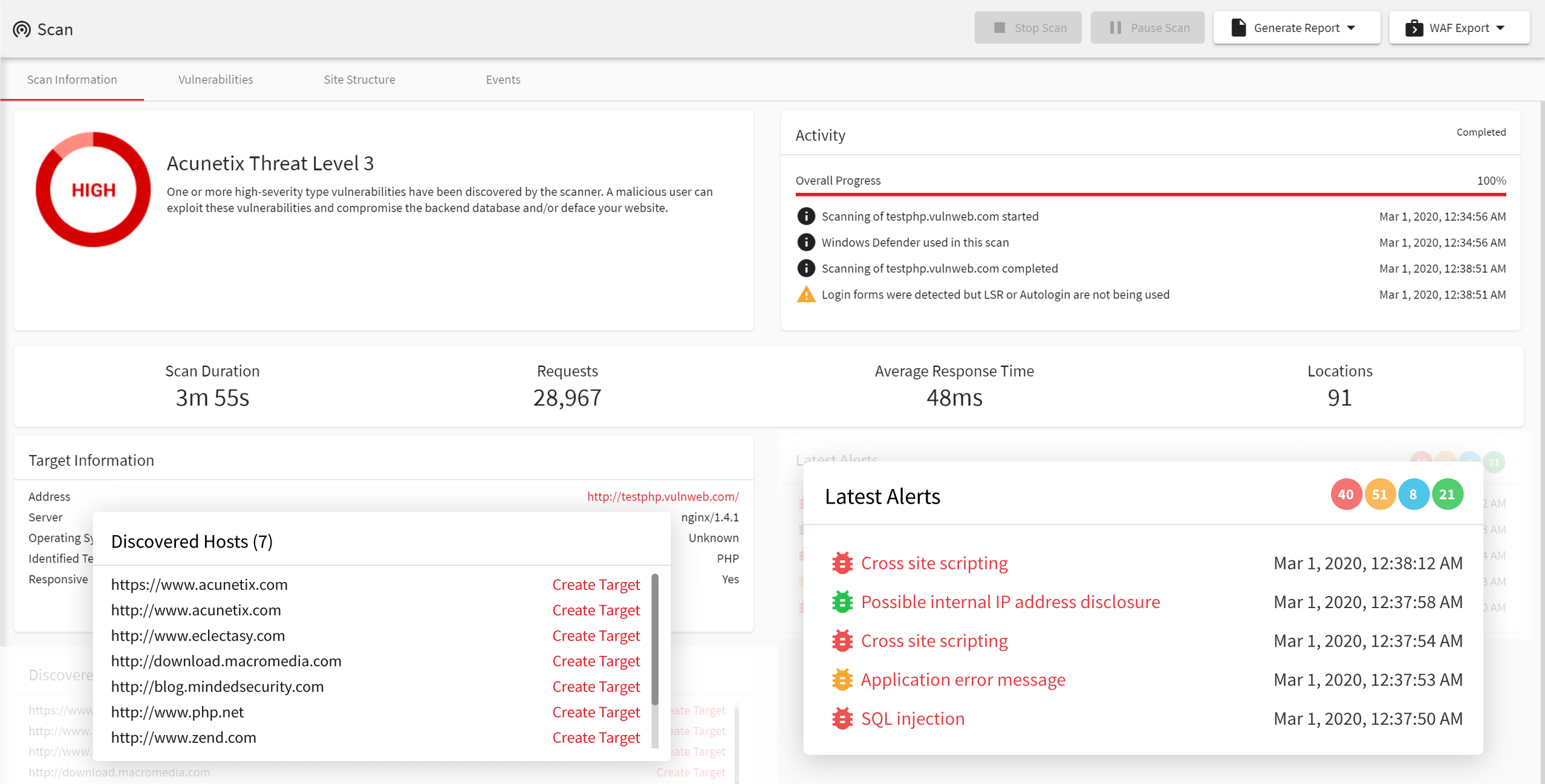
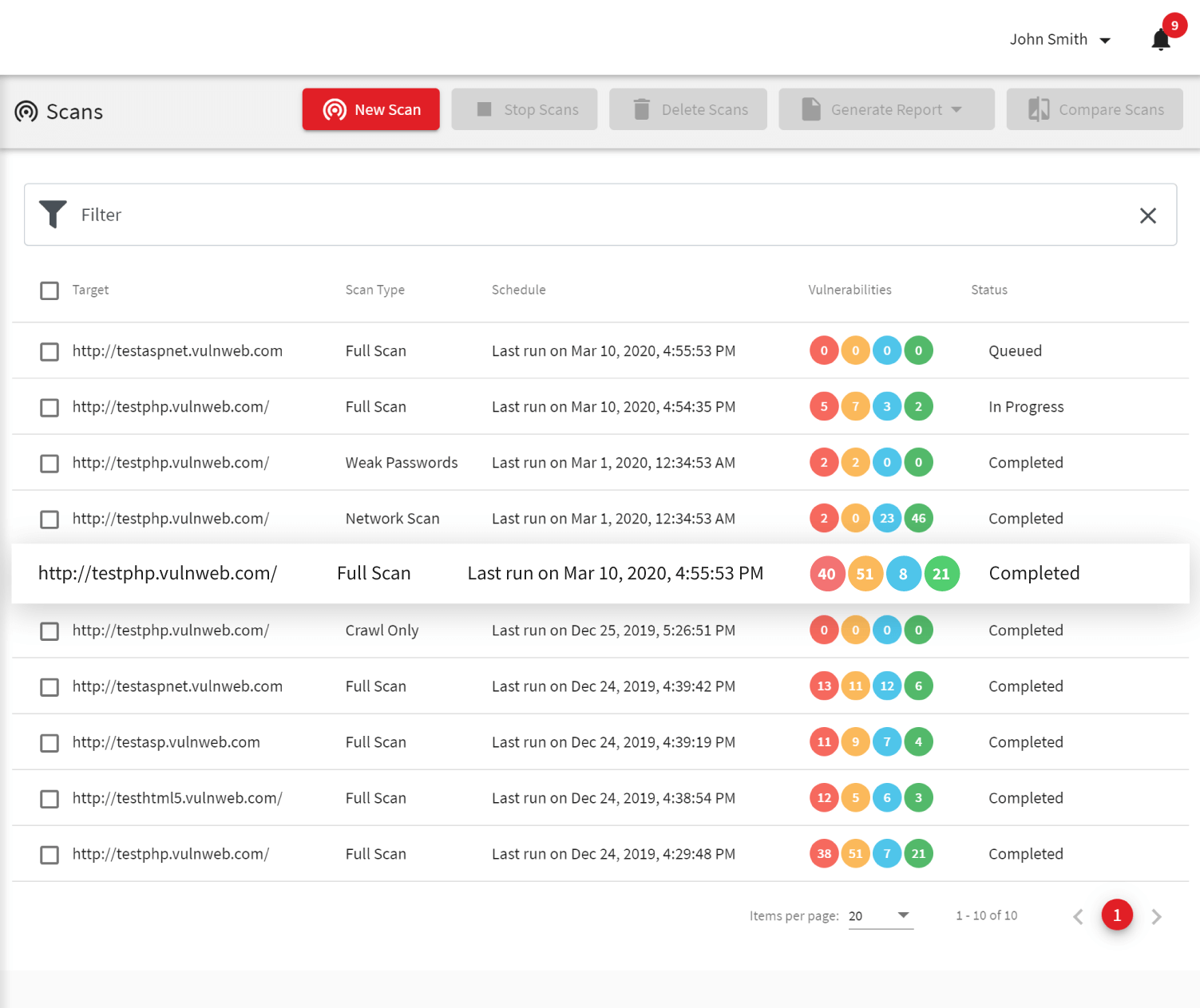
Acunetix Web Vulnerability Scanner is a comprehensive security tool designed to identify and assess vulnerabilities in web applications. It automates the process of scanning websites for potential security flaws such as SQL injection, cross-site scripting (XSS), and other vulnerabilities that could be exploited by attackers. Acunetix is widely used by cybersecurity professionals, developers, and system administrators to ensure the security of their web applications and to comply with security standards.
Features:
- Automated Scanning: Automatically scans websites and web applications for over 7,000 vulnerabilities.
- Advanced Vulnerability Detection: Detects a wide range of vulnerabilities, including SQL injection, XSS, cross-site request forgery (CSRF), and more.
- Comprehensive Reporting: Provides detailed reports on identified vulnerabilities, including their severity, risk level, and remediation steps.
- Authentication Support: Supports scanning of authenticated areas of web applications by simulating login sequences.
- Integrated Vulnerability Management: Offers a complete vulnerability management solution, including tracking, assigning, and resolving vulnerabilities.
- Wide Range of Supported Technologies: Compatible with various web technologies and platforms, including HTML5, JavaScript, and REST APIs.
Technical Application Details:
- Software Full Name: Acunetix Web Vulnerability Scanner
- Setup File Name: Acunetix_Web_Vulnerability_Scanner_Setup.exe
- Full Setup Size: 300 MB
- Setup Type: Offline Installer / Full Standalone Setup
- Compatibility Architecture: 32-bit (x86) / 64-bit (x64)
System Requirements for Acunetix Web Vulnerability Scanner:
- Operating System: Windows 7, 8, 8.1, 10, Server 2012, Server 2016
- Memory (RAM): 2 GB of RAM is required (4 GB recommended).
- Hard Disk Space: 200 MB of free space required.
- Processor: Intel Dual Core processor or later.
- Developers: Acunetix Ltd.
Important Note: Acunetix Web Vulnerability Scanner is a powerful tool intended for legitimate security testing and vulnerability management. It should be used responsibly and ethically, with permission from the owners of the web applications being tested. Unauthorized scanning of websites or applications without explicit consent is illegal and unethical and can result in severe legal consequences. Always ensure compliance with all relevant laws, regulations, and ethical standards when using security tools.











0 comments: